Artificial Intelligence Security Operation Centre (AISOC) stands at the forefront of innovation, harnessing cutting-edge technologies, including sophisticated cyber defence, surveillance, Artificial Intelligence (AI) and Machine Learning (ML).
This formidable arsenal empowers organisations to fortify their digital defences, ensuring a secure, resilient and efficient operation.

Mission Statement
We aim to revolutionise cybersecurity by making it universally accessible, providing affordable and effective solutions to protect individuals and businesses from ever evolving digital threats.
Vision Statement
We aspire to lead the way in shaping a future where cybersecurity is inclusive, innovative, and ubiquitous, ensuring that no one is left vulnerable to digital threats.

Artificial Intelligence
AI, or artificial intelligence, has seen significant advancements in recent years.
Some key areas of progress include machine learning algorithms becoming more sophisticated, leading to improved accuracy in various tasks such as image recognition and natural language processing.
Deep learning techniques have enabled the development of complex neural networks capable of tackling intricate problems. Reinforcement learning has allowed AI systems to learn and adapt through interaction with their environments. Additionally, AI applications in various fields like healthcare, finance, and autonomous vehicles are becoming more prevalent, showcasing the potential of AI to transform industries.

Companies around the world face mounting pressures to defend their most important assets – whether that be physical assets or confidential organisational data. For many of these entities, the best line of defence against increasingly sophisticated security threats is a Security Operations Centre (SOC).
These powerful security centres play a critical role in avoiding security failures that directly impact your brand, operations, and the overall growth of your company. The three key components to have a successful SOC are the people, technology and processes. Any operator of a SOC will tell you that, alongside all the benefits of a high-performing centre, there are several challenges as well.
Challenge 1: The high costs of building an in-house SOC or outsourcing your SOC.
The combined costs of talent and the security tools are expensive. Managing a 24/7 SOC requires a very large team, a secure facility and expensive security tools often adds to up to a multi-million-dollar investment.
Challenge 2: The Talent Shortage and Security Skills Gap
A well-equipped SOC team can provide 24/7 detection, response, and monitoring of your operations and the IT infrastructure and data. SOCs often fall short when trying to find and retain the skilled professionals necessary to run the operation centre.
Challenge 3: The Integration and Interoperability of Security Tools SOCs leverage a diverse arsenal of security tools, like:
Security Information and Event Management (SIEM) systems.
Intrusion detection systems.
Endpoint detection and response (EDR).
User and entity behaviour analytics (UEBA).
Threat intelligence platforms.
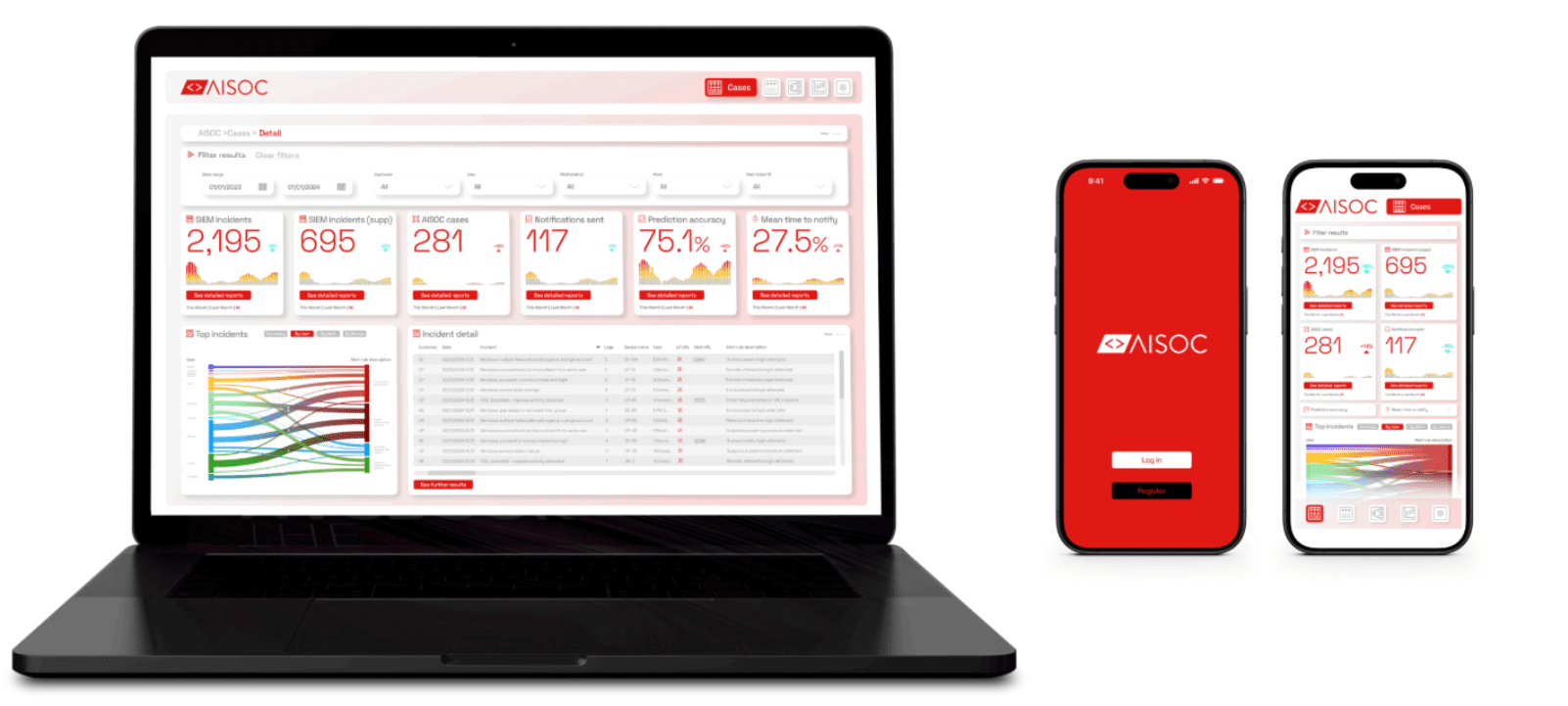
The Cases Tab
From the Cases tab, users have an overview of incidents generated by the SIEM and contextualised by AISOC. The page can be filtered to narrow down the information displayed. The page also offers KPIs on SIEM incidents, suppressed incidents, notifications sent by AISOC to users when AISOC deemed it necessary, as well as the average time it took for AISOC to process incidents.
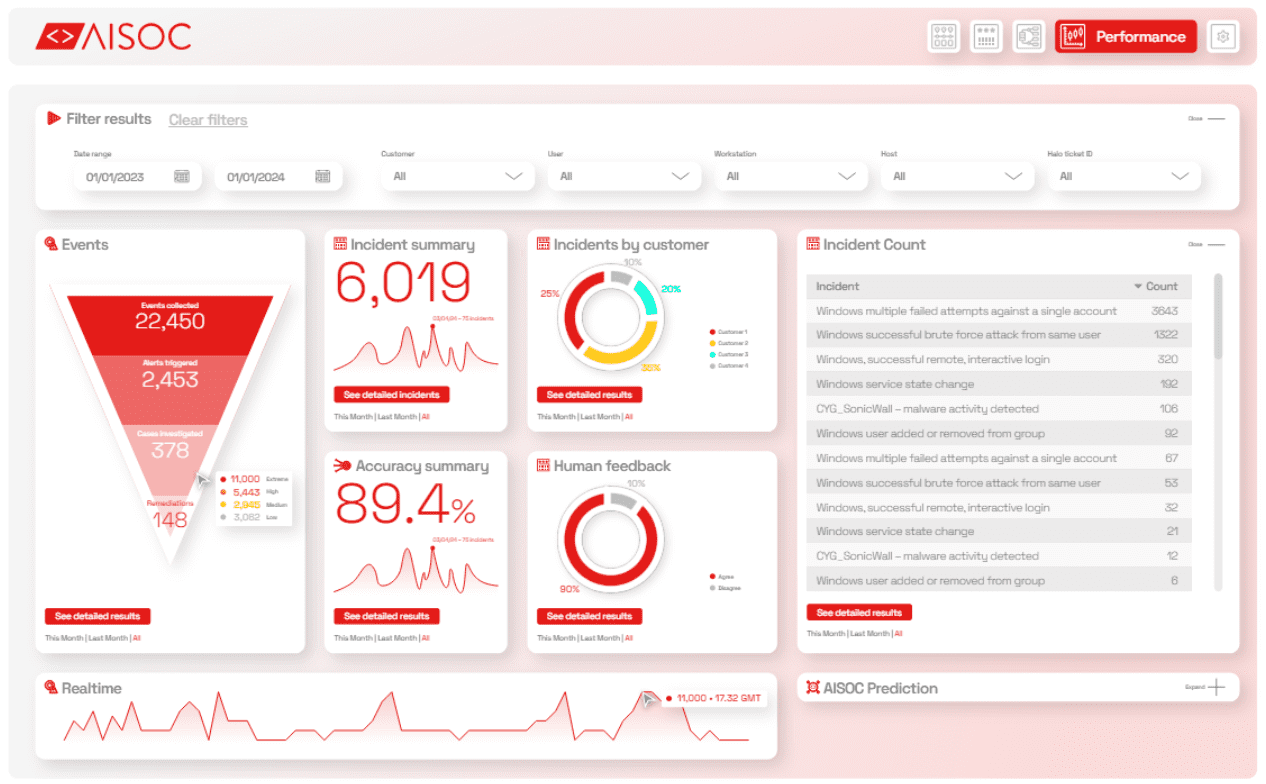
The Performance Tab
From the Performance tab, users can view at a glance the reduction of noise provided by AISOC through aggregations, with KPIs such as the total count of incidents generated by the SIEM and the number of cases requiring investigation created by AISOC. Users also have an overview of user feedback on predictions made by AISOC, accuracy, and common incidents.
Device Compatibility
Our AISOC platform is designed to be fully compatible with both laptop/computer and mobile devices, ensuring that users can access crucial incident and performance data on the go or at their desks with ease. This flexibility allows for seamless monitoring and management of security incidents anytime, anywhere.